Uncivil Engineering: A Textual Divide in Game Studies
by John Aycock, Patrick FinnAbstract
A computer scientist and an artist walk into a bar… Computer game criticism describes and analyzes texts that structure games. Problems arise when comparing or equating computer code and text: source code, for example, is effectively hidden and operates on different rules than accessible code and text. Unlike hidden texts such as palimpsests, allusions, or secret levels in a game, these texts resist traditional categorization. Using examples from the Atari 2600 (VCS) and other platforms, this article uncovers these contributions and suggests several new types of text for scholars to consider. Blending programming and textual analysis the authors locate, isolate, and analyze hidden texts and argue they are an essential part of formal computer game criticism. Framing their work, the authors discuss the benefits and challenges of working across the disciplinary divide.
Keywords: programming, code, retrogames, text, formalism, literary theory, game studies
Introduction
Two households, both alike in dignity,
In fair Verona, where we lay our scene,
From ancient grudge break to new mutiny,
Where civil blood makes civil hands unclean.
From forth the fatal loins of these two foes
A pair of star-cross'd lovers take their life;
Whose misadventured piteous overthrows
Do with their death bury their parents' strife.
The fearful passage of their death-mark'd love,
And the continuance of their parents' rage,
Which, but their children's end, nought could remove,
Is now the two hours' traffic of our stage;
The which if you with patient ears attend,
What here shall miss, our toil shall strive to mend.
- Shakespeare, Romeo and Juliet, Prologue.
We are a house divided. Game studies, like the opening sonnet from Shakespeare’s famous exploration of civil war, stands as a microcosm of the systemic conflict around it, containing both its causal elements, and the recipe for a peaceful resolution. While the scholarly discussion of the need for STEM and STEAM has gone mainstream, those working in game studies find themselves on the front lines of old battles held in place by disciplinary structures, and sites of potential collaboration informed by scholarly tradition [1]. Game studies’ local battles, between narrative and play-based factions, have largely resolved themselves into a dew, as we have come to realize the benefits of collaborating to engage more precisely, and more playfully, with one another’s work. We believe that some attention is required to create a more civil union within game studies, not because of any failings on the part of those within the field, but as a means to fortify our position within the larger framework. This article, a collaboration between a computer scientist and scholar trained in both the fine arts and humanities, attempts to achieve these goals.
The approach is an empirical one, drawing on the idea that both the scientist and artist use formal experimentation as a means of inquiry. For those in the academy this approach will be familiar as formalism, but for those working with computer games the practice is merely a replication of the required collaboration between computer programmers and content creators.
Our paper offers three views of scholarly antagonism as a way to argue for reflective methodological work that promotes our field while protecting it from the slings and arrows of outrageous intellectual fortune. The sections are distinct. The first is an exploration of large-scale issues playing out behind the discussion of texts and their relation to games. The second is a focused analysis demonstrating the specific challenges of text-based study in the field of game studies, and the final section captures the nature of collaboration required to support our research. As scholars who live on the opposite sides of the science / humanities divide, we struggled to collaborate in the way we knew would best serve the work. By placing contextual and focused analysis into contrast, we hope to demonstrate the need to test methodological approaches against models at scale. Beginning with the example of paratext as a lens for reading computer games, we expand on an area requiring contextual expertise related to literary criticism, and programming knowledge capable to read the code at the heart of the study. It may be that formal game analysis requires a team-based approach and that a focused study of collaboration is warranted.
1.0 Darmok and Jalad at Tanagra: The Problem of Incommensurability
In one of his final published essays, Mark Poster discussed his ideas about contemporary media, scholarship, and literary theory. Poster, who as a theorist was one of the key figures in the American poststructural movement, turned his attention to media and technology during the second half of his career. His final lectures, publications and notes focused almost exclusively on these subjects. In “McLuhan and the Cultural Theory of Media,” Poster argues that we inhabit a particularly challenging moment. He uncovered the breadth and depth of the problem while trying to write about digital technology from the perspective of a cultural theorist trained in the contemporary university.
What Poster observed was the rigidity of the separation known to most academics through the work of C.P. Snow. Snow, the chemist, and later novelist, argued in his 1959 Rede Lecture entitled “The Two Cultures and the Scientific Revolution,” that the Western intellectual tradition’s separation of the humanities and sciences prevents us from addressing key problems. His assertions seem to have been met with general approval, though little was done to resolve the problem. Snow’s lecture, later published in a popular edition, was the forbearer to subsequent explorations by Thomas Kuhn, Stephen J. Gould and the aforementioned advocates of STEAM, among others [2]. What Snow outlined as a separation between science and humanities was so profound that Poster felt it left the groups incapable of communicating. This bifurcation was made tangible to Poster during nearly three decades of research into information technology, the Internet, and contemporary media. Where scholars like Kuhn, Gould and those dealing with what is known as the problem of incommensurability identify in a broad sense, Poster starts at the point of direct contact: formal science and media arts. Collaboration across a line of incommensurability can be solved in many ways, as is evident in disciplines such as architecture and psychology, but the combination of basic science and artistic creation which sit at the extreme poles, and which form the basis of contemporary games, resists a theory of unification and instead promotes a collaborative approach based on a form of practical translation [3]. Thus, ours is primarily an empirical rather than theoretical approach.
Beginning with 1990’s The Mode of Information: Poststructuralism and Social Contexts, Mark Poster changed his research trajectory. In six previous books he focused on literary and cultural theory, but now began a focused study of information technology and culture that would produce five monographs, a co-edited book, lecture series, and the McLuhan essay among a trove of unpublished work left by his untimely passing. His lecture series are no longer freely available online, but are now archived at the University of California, Irvine where he worked. Studying his final lectures, we hear Poster speak about the observations made in the McLuhan article, and expanding on the relevant challenges.
What we find as we follow Poster from 1990 forward, is a scholar slowly building the evidence to suggest a unique crisis of ideas caused not only by Snow’s cultural separation, but by a unique moment of technological transformation that exacerbates their conditions. Trained as an historian of ideas, Poster is well-suited to the task. His work provides contextual information that has more to offer than has been integrated into current scholarship.
Poster’s assertions in his final essay are that we are experiencing the largest technological transition in human history at a time when our cultural critics and philosophers are incapable of commenting on the changes. In order to make the case, Poster created a list of contemporary theorists and pointed out that none of them had provided commentary on the nature of the information age, even though it was the largest cultural issue in history. What few commentaries he did find were underdeveloped.
In Deleuze and New Technology (2009), the collection he co-edited with David Savat, Poster tries to address the gap. While Deleuze’s examination of technology was relatively minor, it provided a starting place, allowing Poster to engage theorists he hoped would take up the case. The other major contribution was the discussion of McLuhan. With his increasing focus on technology in the 1990s and 2000s, Poster began to notice that none of the major thinkers of the day referenced the work of Marshall McLuhan. Given McLuhan’s influence on the scientific side of Snow’s cultural divide, this finding stood out. During the last part of his career, Poster shared a study indicating the lack of citations to McLuhan’s work in the publications of the most influential cultural theorists. How was it that McLuhan, a scholar acknowledged as one of the founders of media studies was so thoroughly ignored by those providing cultural commentary in the information age?
There are two primary reasons for the rejection of McLuhan. The first is cultural and the second and more challenging is epistemological. The former, following Snow’s example, was a matter of taste. McLuhan was seen as a techno-fetishist who sold his soul to industry, while Raymond Williams, who is usually labelled McLuhan’s co-founder of media studies, offered a cultural analysis based on Marxist literary theory. The culture wars played a significant role in the dismissal of McLuhan, but for our purposes, it is the second challenge from Poster’s work that requires attention.
Regardless of political or philosophical positions, the difference between art and technology is pedagogical and epistemological. Those conversant in science and technology are educated in streams that deliberately guide them away from the arts and humanities, while those with a predisposition for letters are steered away from math and science. In our scholarly drive towards specialization we solidified Snow’s separation by training our minds away from one another. In doing so we are left to face the possibility that not only are we not in conversation with those on the other side of campus, we may lack the training necessary to do so.
In an episode of Star Trek: The Next Generation entitled “Darmok,” we are presented with a case of linguistic incommensurability that provides a useful frame for this conversation. The episode’s popularity made it a popular science fiction meme, providing a metaphor for communicating across linguistic barriers. The episode is predicated on the need of two figures to begin to communicate. The challenge is great because they not only lack an understanding of the other’s language, the languages in question do not fit within a linguistic framework that supports translation [4]. They face incommensurability. Here we might think of the difference between cognate languages as disciplinary difference, while the Darmok difference is an essential one. We can understand those working in different disciplines as long as they are somewhat similar to our own but going too far afield renders translation more difficult. Following C.P. Snow, the separation leaves us hampered by not knowing what we do not know.
At the outset of the “Darmok” episode, there are two communities in need of communication: the Tamarians, and those aboard the Star Trek Enterprise. The groups have been attempting to communicate without success. Their current translation technology is of no assistance. Notably, this translation software works everywhere else the crew journeys, demonstrating just how far apart these language systems are supposed to be. Desperate to convey a particular message, Captain Dathon of the Tamarian ship kidnaps Captain Picard of the Enterprise and has them beamed down to the surface of a planet below their ships.
The stakes are high because the Tamarian captain selected a planet inhabited by a monster capable of killing them if they do not work together. A number of studies attest to the fecundity of the episode’s treatment of language and communication by necessity. Scholars such as Erica Schoenberger demonstrate its ability to offer models for collaboration between divergent scholarly fields. For their part, programmers created software titled Darmok, and now Darmok2 to support play or case-based approaches to meaning. We are not the only ones struggling to communicate. “Darmok” is a symbol of the incommensurability problem.
If Poster is right when he describes the distance between those of us that can code and those who are storytellers, what chance does game studies have? The answer is comforting. Game studies figured out ways to bridge the gap and begin conversations before agreeing upon a common language or frame of reference. The reason this bears attention is that resolving the separation identified by Poster, by using successes resulting from our being thrust together in “Darmok” moments offers us a chance to refine our approaches, and potentially providing others with techniques for collaboration. Given that the greatest challenge to overcoming the impediments to collaboration are structural, these efforts are necessary to support work that offers ways to overcome bureaucratic barriers that change slowly.
The two captains in “Darmok” share one thing: a deep desire to communicate. They are a house divided, but they decide to work together because division does not serve either group. The resolution of the episode provides the first lines of communication, but it is clear work will continue to improve the connection. That work, the arduous labour over linguistic detail, is work for the scholars. Formalism is like that, necessary for all, but loved by few.
1.1 Darmok and the Disciplines
Work in Game Studies crosses not only disciplinary boundaries, but the fault line described by Snow and Poster. Within our community, we continue to explore the narratology / ludology debate, though it is increasingly rare to find someone willing to declare commitment to one or the other exclusively. It is perhaps a symptom of our good fortune that game studies seems capable of sustaining several wide-ranging approaches without the need to disavow alternate methodological assertions. Simultaneously, much discussion has been dedicated to the extent of “games” as a region of analysis, with an agreement that “games” includes board games and other such interactive creations. Game studies seems to be resolving into a conversation about how to heal the material / non-material divide that separates subjects in the traditional university. Best of all, it does so in a manner framed by the exploration of play.
The study of play is essential to game studies and provides its greatest challenge. Articulating the function of code at the heart of a computer game is about as far from playful as one can imagine. Yet, it is only through engaging limitations that play is possible. Evaluating the success, failure, and nature of limitations within a game requires a formal approach to the interaction between hardware and software limitations. Beyond mere technical evaluation, this approach opens the possibility of offering critical attention to those whose work is ignored when we only evaluate the final output of the game. The aesthetics of games lies somewhere between the material and immaterial worlds of hardware, software, and creative composition. To gain a greater appreciation for why certain decisions are made, it is important for us to gain a better picture of the details framing those choices. In short, we need to pay as much attention to code as to words and begin our work from the point at which they support play.
If we can borrow from literary studies for terminology, perhaps we can also borrow pedagogy. We do not all need to be experts in the formal machinery underlying our research area, but we all have to understand it. Our study looks at paratext as an example highlighting a need for a dualistic approach to research methods. The first must take into account textual execution, including readings of texts that capture aspects as diverse as text, image, and material construction; and, the second is play-based, focused more on the lived or performed aspect of the game. Both sides require a system that combines the material and immaterial, and both contain the requirement that reception or audience are included in the evaluative structure.
Whatever our approach, or state of scholarship, the central challenge cannot be solved by working together using the models of the disciplinary academy. We must “Darmok” the problem, while recognizing the heavy lifting that entails. We must, like the Montagues and Capulets in Romeo and Juliet, realize that we have to integrate our knowledge to live in the world. It may be that in the future, computer game critics will train in the humanities and computer science, but it seems more likely that collaborative approaches to criticism and evaluation will be necessary. Besides addressing a skills gap that may be impossible to close, it offers a critical approach more in keeping with the creative form it addresses. Games are a collaborative art form, which may fundamentally require a collaborative approach to critique. Game studies promises a new approach to text and grammar that will help us work better to serve our research interests.
1.2 Text Me: The “Abstract and Brief Chronicles of the Time”
One of the richest streams in game studies is textual analysis. Whether through media-based approaches of Janet Murray (1997), the social analysis of Sherry Turkle (1984; 1995; 2009; 2011; 2015), the modular interventions of Ian Bogost (2006; 2015; 2016), or the ergodic literature model developed by Espen Aarseth (1997), the analysis of text in relation to computer games is simultaneously well-established, and hotly contested [5]. Wherever the discussion manifests, there is an appreciation of text, and of our need to compare different types of texts, as a way to describe, analyze or evaluate digital media. The question is: how do we do the work? We hope to contribute to this work by sharing a challenge to focus on text when studying computer games.
Paratext, based on the work of Gérard Genette (1987, 1997) is often used to describe the types of text present in a computer game. We will trace its ability to engage games built for the Atari Video Computer System, or VCS, perhaps better known by its later “Atari 2600” name. In so doing, we join those such as Montfort and Bogost who are interested in platform studies by bringing attention to the constraints of the Atari 2600 platform and the code used in the creation of its games, while at the same time maintaining a commitment to textual formalism’s analysis of deliberately crafted work. Here, the context of formal compositional conditions meets textual detail as in the analysis of those such as Espen Aarseth [6].
Our “Darmok” challenge is: how do we speak meaningfully about the intersection of different kinds of text? Early explorations of the challenges posed by games that contain lines of narrative text as well as lines of computer code turned to literary theory to find descriptions of text that captured the complex nature of material text in relation to literary or non-material text. While some approaches, such as that of Montfort and Bogost, have offered a more robust engagement with game function, there are challenges in the categorization of text that can be demonstrated by studying game samples from the Atari 2600 [7].
In the same way that the ludological approach to game studies benefits from the material study of early games, the study of material texts through codicology and paleography also provides essential elements for game studies. The work of W.B. McKerrow and Jerome McGann on bibliographic codes provides a rich study of the textual meaning found in and around the formal text recognized by literary studies [8]. These approaches account for production and social aspects of text, incorporating the interpretation of images, book structure, and reader engagement. Taken together they offer a robust set of tools for evaluating the textual conditions of works that include various media and audience interaction. The theoretical implications of this approach engage the complex nature of text in game studies, a field which must reconcile textual taxonomies between vastly different systems.
In many game studies approaches, literary theory provides the models used to conduct the analysis of text. Here we can distinguish two general approaches: the poststructural complexity model, and a structuralist model updated to include game elements. While not an exact match, we can map the narrative approach with the complex poststructural model, while the ludological connects to structuralist approaches modified for contemporary conditions through materialist critiques like that of McKerrow and McGann.
Gérard Genette began as a structuralist focused on discourse and narratology, and later developed a textual theory crossing into poststructural analysis while maintaining a critique of material conditions. Poststructural theorists as noted by Poster, tend to avoid technology, but draw on linguistic complexity; while structural analysis crosses into social scientific approaches using statistical analysis, and conducting research involving human subjects requiring methodological adjustments. When McKerrow and McGann brought the social approach to text, the mixture was potent, and created an approach to scholarship that offers lessons for the Science / Humanities divide. It is in this realm that Genette’s work became an effective option for scholars seeking to evaluate computer games. The obstacles we discuss arise as we attempt to identify types of materiality when evaluating computer games.
1.3 Bill Gates Capitalizes
Bill Gates’ one-page 1976 letter to the Homebrew Computer Club is one of the most influential publications of the 20th Century [9]. In its wake, we face profound challenges when speaking about the material world using literary theory. For Gates, “capital” means information, which he wished to see protected by copyright law, while for humanists it usually refers to tangible elements in the means of production. Leaving aside ideological discussions, the constitutive elements of information and material create a rift in the received approach to textuality, including those involving social text models. Mark Poster saw the challenge to academic studies based on an analysis of capital once capital might point to the intangible. Game studies began taking these realities into account, but the prevailing critical discourse needs development. Materialist analysis remains essential, but we need to address the implications for formal analysis in order to ground such discussions.
The question driving our approach is: how does one conduct a formal analysis of a computer game? We can take as a given game studies’ interest in the formal analysis of games, but as noted, we have yet to settle on normative approach. While we cannot offer a solution, we can identify a gap containing hints for future work.
While literary theory provides a detailed analysis of text and meaning, it falls short when we treat code as text. While we agree that textual analysis is fundamental and is capable of analyzing material and non-material information, it struggles with computer code. When we read the code within a game, its nature is categorically different than literary or social text. We hypothesize that its proximity to mathematics accentuates the contextual divide between humanities and science, while also creating profound interpretive errors at the level of practice. Code, like mathematical notation, is a nearly pure abstraction. It operates under a different set of principles. Book-based criticism works for a book-based creative form, but no matter how extensively modified, it struggles to access digital creations. Thus, while McKerrow, McGann and even Genette are able to extend textual studies to include images, objects and beings, their system remains tethered to books as the primary technological interface. Games are used differently and require new rules of engagement.
Moving from the contextual frame to the precise articulation of our case, we turn to a focused discussion of specific problems in game studies found at the heart of the text / code divide. By exploring the use of paratext introduced by Gérard Genette, and modified by game studies scholars, we illustrate the challenges inherent in selecting critical models from pre-existing fields when crossing disciplines across the great Science / Humanities divide.
2.0 Digging into Computer Games: The Case of Paratext
Computers operate in terms of ones and zeroes, a binary representation of instructions and data which is non-optimal for human programmers. While slightly more manageable numeric representations exist, such as octal (base 8) and hexadecimal (base 16), writing a program of any length using these representations is rare. Early in computing history, programming languages were designed to be easier for programmers to use. For the purposes of this section, we will confine our discussion to assembly language, which was used for efficiency by many early retro games. The problems we identify are exacerbated when higher-level languages are considered, but assembly allows us an accessible example that covers all of the key areas. Figure 1 shows a comparison of the different representations of a single assembly language instruction.
| Assembly language | jsr clear_screen |
|---|---|
| Hexadecimal | 20 58 fc |
| Octal | 040 130 374 |
| Binary | 0010 0000 0101 1000 1111 1100 |
Figure 1. Equivalent forms of an assembly instruction
A programmer writes assembly code in one or more source code files. Each individual file is then assembled by an assembly program, creating a binary representation the computer can run. Beginning with the multiple source files, the assembler produces a less than complete translation of each file. Specifically, the assembler does not have complete information about other files being assembled, and a linker program effectively “stitches together” the partially translated files into the final runnable binary representation needed by the computer (Figure 2).
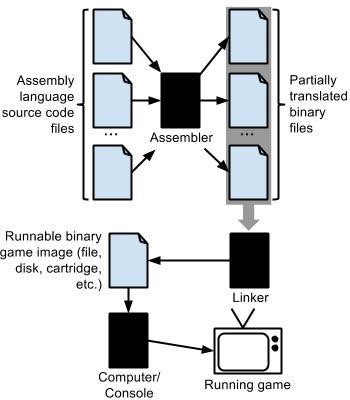
Figure 2. From source code to running game
Already we can see problems in treating the game as text by studying its characteristics and behavior, because effectively we have three layers of entities that have a claim to being “text.” There is the source code that the author creates, there is the assembled binary code, and finally the observable game itself [10]. To consider the ramifications of this for game studies, let us examine some of the things that are--and are not--present in these texts.
2.1 Law, Sausage, and Computer Games: You Don’t Want to See Them Made
The binary sold and distributed as “the game” has already lost a significant amount from the source code the game author(s) created. Source code is a rich repository of information, such as human-readable comments left by the programmer and the names of labels, constants, and variables in the code. These are not needed by the computer to run the binary version of the game and are consequently removed during translation. What may be more surprising is that all the instructions in the source code may not appear in the assembled, binary version. Code may be written to assemble conditionally, so as to create different versions of the game such as Phase Alternating Line (PAL) versions for use in Europe and Australia, National Television System Committee (NTSC) for the United States and NTSC-J for Japan. In other cases, instructions in the source code may be “commented out” by the programmer, so that they are ignored and not translated by the assembler. Commented-out code yields revealing tidbits: practices of code optimization by the programmer, and a record of features intended but abandoned. The binary game, even if disassembled, or translated in reverse from binary to assembly code, cannot restore the original text.
If the source code is irretrievably lost, what of the binary code? Is any of it altered when it is transformed via the computer’s execution from static bits into a dynamic running game? The answer is no, maybe, and yes. Because the computer blindly runs the instructions it is told to, and the binary is the repository of those instructions, the running game can be claimed to be a valid representation of the binary if not the source code. Or at least the current state of the binary, because one technique used in older games was self-modifying code, where the game would modify its own instructions during execution. Here we face the difficulty analyzing a book’s text that changes as it is read.
Some games are said to exhibit so-called emergent behavior, where a complex or unintended behavior results from code in a way that was not explicitly programmed to allow it, but ultimately that behavior does arise from the code in the binary. It is accurate if unintentional. Another case is that of bugs in a game. For example, Halo 2600 had a bug that allowed a player to enter a “Magic Land” to explore (Fries, 2010). Here again, even if unintended by the programmer, the behavior derives from the contents of the binary.
While the game is a valid representation of the binary’s contents, it may not be a complete one. There may be both code and data in the binary that are not used in any way in the game. For instance, the Atari 2600 game Chase the Chuck Wagon (Schwartz, 1983) has five unused areas in its binary of nontrivial size: one is an unused image of the canine protagonist, the other four’s purpose is currently unknown [11]. Bailey (2008) refers to code that is present in a game but unrunnable as a “fossil,” although this is cast as an intentional act on the part of the programmer [12]; given that Chase the Chuck Wagon was created over a weekend (M. Schwartz, personal communication, 21 January 2014), haste is as likely a cause as deliberate intent.
Perhaps more intriguing are readable messages in the binary that do not appear in-game. We draw here from a methodical survey of 1,816 Atari 2600 game images conducted (Aycock, 2014) using novel message-finding software (Aycock, 2015) in conjunction with software created for computer security research. The Atari 2600 is a particularly interesting subject to study in this regard because of how challenging it was to program, and the limited facilities it had (Montfort and Bogost, 2009). For one of these messages found in the binary to appear in readable form on screen would require heroic programming efforts that few 2600 games contain.
The nature of some messages is deliberate and unsurprising: copyright and attribution. For instance, “COPYRIGHT 1989 TNT GAMES DEVELOPED BY SCULPTURED SOFTWARE WRITTEN BY ADAM CLAYTON.” There was the odd surprise in this category, however, like the reversed author credit “N GUOD” in some of Douglas Neubauer’s games. These would have all been deliberately placed by the programmers in the source code and carried through by the assembler and linker into the binary. The assembly source code for Solaris (Neubauer, 1986) accomplishes this with the directive:
.byte "DOUG N"
Some messages appear to be inserted as side effects of running development tools, like “LINK 1.6,” suggesting linker usage. Any such messages would be deliberate, but the game author would have no direct agency beyond running the tool, even though the resulting game would be taken as the author’s work.
Quite a few messages in game binaries likely arise as a result of serendipity. In modern times, failure to clear computer memory can be seen as a security issue (MITRE, 2014), but during the 2600’s time this would not have been a consideration for most systems. The happy result from a historical preservation point of view is that game binaries have accidentally included a variety of fragments that happened to have been in memory, of which the most interesting are chunks of assembly source code.
Then there are messages that manifest themselves through random chance. For example, the word “BIGAMY” is encoded in the binary image of the Combat Two prototype (Atari, 1982). This is almost certainly coincidental, rather than a nod to multiple simultaneous marriages, both because of the unusual encoding and also because all of the characters in the word were used as non-message data when tanks fired shots in the game [13].
Clearly these messages are “text” of some kind or kinds, but their classification is uncertain. While present in the binary, they do not appear in the game. Taking the game-as-text approach cannot encompass them, so we have to find a place for them in our system. Genette’s paratext is a prime candidate.
2.2 The Pitfalls of Paratext
In Genette’s original formulation of paratext (1987/1997), the key is liminality, where the paratext helps to frame and contextualize the text and can be seen as delimiting a boundary, a threshold to be crossed. He further breaks it down in terms of the equation
paratext = peritext + epitext
where peritextual elements are within the volume containing the text, and epitextual elements are without. In all cases, Genette’s paratext relies on the unstated, tacit assumption that a person for whom this threshold will beckon is able to perceive it. In book-based approaches, this makes sense. Why would text or paratext exist if it cannot be seen and read by its audience? It does not work as well in the case of games. Even the few examples given above stretch paratext beyond its useful bounds.
We are not referring here to exceptions that are made in game studies, where an individual researcher may not have the requisite skill to play all parts of a game, or the time to play through all the different outcomes of a game (Fernández-Vara, 2015). Nor does this fit the category of “Easter eggs” that go untriggered in specific game play experiences. In these cases, all material is available for consideration.
For Atari 2600 games, the game cartridge was a sealed unit. A programmer embedding a text message in the game, inaccessible through play, had no reasonable expectation that it would be seen by an audience. There is an important distinction to make on this point: a message is paratext only if it has a reasonable likelihood of being perceived by some audience. By this standard, the messages in the previous section cannot be paratext. They exist beyond the possibility of categorization in this system. We can see these messages now because modern emulators and other tools have effectively rendered contemporary gamers / researchers omnipotent in relation to the game platform’s original context, and original textual content.
All hidden messages are not the same. As games started appearing on floppy disks, the ease of examining and copying them increased, and game developers began to leave targeted messages in their creations that would not be seen in the game. The audience for these messages was anyone trying to copy the game or crack the copy protection to render the game copyable. Consider these messages from Apple II game disks [14]. Cannonball Blitz (Lubeck, 1982) disks contained the hubristic “YOU’LL NEVER BREAK IT”; Mr. Do! (Mirsky, 1985) disks carried the message “DON'T WASTE YOUR TIME, ORIGINALS ARE INEXPENSIVE.” The educational game Geo-Race U.S.A. (Jensen, 1990) had a longer message broken across two disk sectors:
STOP SNOOPING. ONLY A DESPERATE AND FUTILE ATTEMPT ON YOUR PART TO COPY THIS PROGRAM. WARNING: ON EACH DISKETTE IS AN ENCODED SERIAL NUMBER WHICH WILL BE USED TO TRACE DUPLICATE DISKS BACK TO THE PURCHASING PARTY. ALL RIGHTS RESERVED. GO AWAY. YOU ARE VIOLATING THE RIGHTS OF MASTERY DEVELOPMENT. THE ENCRYPTION TECHNIQUES USED TO PACK THE MAPS AND THE GRAPHIC SCREENS ARE TRADE SECRETS AND ILLEAGAL [sic] USE THEREOF IS PROHIBITED. I JUST THOUGHT I’D BETTER FILL THIS UNUSED BLOCK WITH SOMETHING…
These are interesting examples at the limits of paratext, because we can prove these hidden messages were seen by their intended audience. Krakowicz (n.d.) mentions the Cannonball Blitz text in his (?) 1980s treatise on cracking, THE BASICS OF KRACKING [15]. The other two examples were brought to our attention by “4am,” a software cracker specializing in retro Apple II games. More speculative is the recruiting message embedded in the ROMs for the Japanese arcade version of Donkey Kong (Nintendo, 1981) which says [sic] “CONGRATULATION !IF YOU ANALYSE DIFFICULT THIS PROGRAM,WE WOULD TEACH YOU.*****TEL.TOKYO-JAPAN 044(244)2151 EXTENTION 304 SYSTEM DESIGN IKEGAMI CO. LIM.” (The Cutting Room Floor, n.d.). It is unknown whether or not this message found its audience of potential apprentices.
2.3 Textual Taxonomies and the Challenge of Classification
What is clear is that we have a classification problem because there are messages that are not text and not paratext, and which will not fit standard terms used for variations in text. These messages may have been created by the game author, or a software tool that the author used, or even by accident. The messages do not appear during play and exist unseen by an audience. What are they? Where do they exist, and how do they contribute to the meaning of the games in which they are contained? Are they so far outside the textual framework that scholars would agree to discount them if asked to conduct a detailed account of all aspects of a game?
The implication is that a third category needs to exist beyond text and paratext. If we recall that the text / paratext distinction is one that captures a set of textual types, we are faced with the need for a new set of textual types. In some sense we have cryptotexts, endotexts, and spatiotexts to name only a few of the possible realms. More challenging still is the determination of a localized grammar. Are the texts in this new set in conversation with one another? With the work as a whole? Whatever our answer it seems the box of a retrogame cartridge consists of texts, para (or peri) texts, and a set of texts with close ties to the game’s authors, owners and distributors. One might argue that this extra classification is pedantic, and that a game must necessarily only be interpreted by its playable text and appreciable paratext. On the other hand, a finer-grained understanding of the technical composition of a game, what is lost that the author created, and what is gained that the author did not create, is not a bad thing to have as game studies matures. As Bailey (2008, p. 70) forcefully asserts, “game studies will not achieve its full potential until considerations of computer science are more fully integrated into its methods.” Developments in platform studies appear to be addressing some of these concerns, but at its core what is required is a formalism that can serve all those working in game studies. We do not all need to understand code or text in the same way, but an attention to the primary interactions between them will serve us all.
3.0 “Shaka, When the Walls Fell”
The Tragedy of Romeo and Juliet is often described as the beginning of Shakespeare’s mature work. His early explorations of poetry and prose as indicators of character are deepened when he pairs two figures who when connected literally, “complete each other’s sentences.” This development in language allowed Shakespeare to portray shared fate and the interaction of consciousness. Prior to these explorations characters completed speeches separately. The relationships were less interaction and more modular assembly. At the same time, Shakespeare was exploring genre. Tragedies were supposed to focus on a single tragic hero. In Romeo and Juliet, we have a paradox: a tragic hero split into two people, and a tragic flaw not resident in either. Their fate is to collaborate to bring a divided world together.
Whether we look at the case of Romeo and Juliet, or that of the captains in “Darmok,” we confront a need to communicate; to reunite in service of society. Game studies has much to celebrate in this area. Scholars who are separated by physical and intellectual space within the academy come together in the service of intellectual inquiry. Still, following C.P. Snow and Mark Poster, the divide between those of us trained in computer science and those trained in arts and letters is profound. If we hope for a better outcome than Shakespeare’s star-crossed lovers, we need to acknowledge how little we know about each other’s work and how hard we have worked to create the divide separating us.
We would like to suggest that working together to address inherent incommensurability in game studies is essential, but nearly impossible. We work by different clocks and calendars, employ different techniques, and use the same words to mean different things. Game studies seems to have found a way to promote collaboration like ours and supports different approaches within that realm. Our belief is that explorations in collaborative models of research are both our best hope, and our greatest challenge. It may be that like Shakespeare’s poetry, and Espen Aarseth’s “ergodic literature,” the rules are embedded in the work, and must be excavated. Either way, it can only help to have a fuller picture of the contribution of game creation. To conclude, we would like to share some specific aspects of our collaborative process.
4.0 Of Mice and Pen
Our collaboration began as a discussion of review comments from a journal submission by one of the co-authors. If one aspect of our work is the assertion that what we are doing is somehow new, it is also an approach that is founded upon one of the oldest scholarly models for resolving incommensurability: collegiality. That our “house is divided” seems obvious to anyone working in the contemporary academy, but that separation is more a product of late-stage modernist disciplinary structure than an essential component of university life.
The secret of our “success” in this approach was serendipity. We happened to find ourselves working in a program designed to bring together artists and scientists in order to foster innovation. The program, called Computational Media Design (CMD), was built to address the same kinds of incommensurability issues experienced in game studies. Prior to our chance meeting neither of us had any idea we had a colleague working in the same area less than two hundred metres away.
Our work progressed slowly and was based on questions. Each of us asked how we could better explore and express our ideas about games. We seemed to share a general belief that game studies provided a natural environment for such collaboration, but the longer we worked the more we came to realize that we would never fully understand one another in the same way that one might come to know a colleague with similar disciplinary training. We both have experience in each other’s domain of research, but the formal expertise required to work as a researcher in computer science or in the fine arts is too specific to allow for a shared language. We began to speak of this in computer programming terms, once again finding inspiration in games. Computer games are built using different languages and elements, and achieve their expressive power not by finding one language that unites all contributions, but instead by realizing that there is communicative power in specialization that is best left intact and effort made to compile or assemble disparate languages in service of a common goal.
There are many examples of fruitful collaboration between the arts and science, and those models will continue to provide essential contributions. Ours is one other approach that benefits from translation across other languages and approaches, but which asserts that sometimes it can be of use to struggle through incommensurability so as not to lose disciplinary rigor necessary for certain kinds of scholarly research.
In the end, we found this work to be instructive, rewarding, and worth the effort. We would be remiss however if we did not share that the process took more than three times as long as our normal scholarly work [it is not for nothing that our use of the Star Trek metaphor references a successful bridging of incommensurability that ended with one person dead and the other injured!]. Our hope is that formal practice in the area will make collaboration more efficient, but the unfortunate reality of scholarship is that we cannot choose how long it takes to complete work that is worthy of sharing with our colleagues.
Endnotes
[1] Science Technology Engineering & Math, is modified by the addition of Art or Arts to provide: Science Technology Engineering Arts & Math. The STEAM debates continue the C.P. Snow tradition and entered the lexicon with national and international standards beginning at roughly the same time as Poster’s McLuhan article, but with contention over who is responsible for inventing the acronym.
[2] Kuhn’s Structure of Scientific Revolutions is one of the most influential intellectual histories of the modern age. While his focus is on the nature of epistemological change in the world of science, his book articulates the ways that knowledge progresses in the humanities as part of his study. Gould made his reputation both for directly comparing artistic and scientific discovery, and for dedicating time to discussing evolution in the public sphere, including engaging in debates when he felt the science was being mispresented, as happened in his famous battle with colleague E. O. Wilson.
[3] While Kuhn is best known for his discussion of paradigms, it was Paul Feyerbend that most directly discussed incommensurability and along with Kuhn gave rise to a detailed study of the subject that has been traced through the philosophy of science in the work of Donald Davidson who expanded on Kuhn, William Quine who focused on logic and the question of translation between systems, and Hilary Putnam whose analytic approach provides insights that are particularly relevant for computer science. Our approach takes a practical / empirical approach by demonstrating work across the type of “conceptual conservatism” identified by Feyerbend, in hopes of providing models for collaboration that join rather than attempting to resolve discussions about incommensurability.
[4] A feature of the series is that the characters in Star Trek possess a “universal translator” that automatically renders all foreign languages into English. The failure of the translator to address the bridge between the two captains in this episode is referenced several times as a unique challenge.
[5] In an addendum to our discussion of Poster, it is important to note that along with Donna Haraway and N. Katherine Hayles, Janet Murray and Sherry Turkle have established significant research records and public attention. The fact that Poster does not include them in his evaluation of contemporary thinkers says more about their ideological classification along with those interested in technology, than it does about their influence. It is telling that within a world so often charged with sexism, the four most significant theorists are all women. Adding Katherine Davidson from Duke as the most influential integrator of technology and education extends the set.
[6] There are a number of important contributions to the study of games that consider source code, such as Lederle-Ensign et al. (2015) and Willumsen (2017). Additionally, excellent work has been done in platform studies, starting with Montfort and Bogost's examination of the Atari 2600 (2009) and including entries on the Amiga (Maher, 2012) and the Nintendo Entertainment System (Altice, 2015). The most recent entry in the platform studies series as of this writing, Carl Therrien's The Media Snatcher (2019), is of particular note. As recounted in the book, Therrien turned to specialists across the disciplinary divide, amongst them an electrical engineer and a computer scientist -- the latter of whom is a co-author of this paper -- to help find the answers to technical questions. This work in turn led to further interdisciplinary collaboration with an archaeologist, culminating in an archaeology journal publication (Aycock, Reinhard, & Therrien, 2019). We view these as further examples of the kind of work we are advocating for in game studies in the same way we view the contributions in the philosophy of science with regard to incommensurability.
[7] Montfort and Bogost’s book, Racing the Beam, is a direct attempt to resolve many of the issues at stake in our article. Montfort and Bogost assert that we need greater attention to game creation inside game criticism; however, their approach continues to focus on a metaphor-based approach to game construction. While this approach is effective, we believe that the disciplinary study of an academic subject requires detail that is as granular, and direct as possible at its root. With that in place, higher order abstractions become testable and more effective.
[8] The McKerrow--McGann line in textual studies introduced and maintained the argument for extra-textual elements in textual analysis. Thus, their work supported the more productive explorations of digital humanities editions of scholarly work and led to the scholarship most often sighted as productive for game criticism in the work of scholars such as N. Katherine Hayles and Janet Murray.
[9] A scan of the original, “Open Letter to Hobbyists” can be found here: https://commons.wikimedia.org/wiki/File:Bill_Gates_Letter_to_Hobbyists.jpg.
[10] The third kind of text here can be further broken down into the literary forms of text specified by Genette, but we will focus on the first categories for simplicity of argument.
[11] Reverse engineering of the game binary was done by Cameron Hawthorne and verified by one of the co-authors.
[12] Although Bailey refers to fossils in parts of his work as “unintentional,” the detailed discussion of them implies programmer intent, so we have used that characterization here.
[13] This example was first discovered by one of the co-authors in a survey of the Atari 2600 cartridge who verified the usage of the bytes in-emulator (Aycock, 2014). While one could argue that the encoding is too contrived (each byte, exclusive-ORed with 65, yields the corresponding ASCII value of the character in BIGAMY), the fact remains that the ASCII code---while fairly arbitrary itself--is very widely used, and the survey found legitimate messages with similar encodings (like exclusive-ORing with 64).
[14] We confirmed the existence of all these messages as well as the later Donkey Kong example. In the latter case, we have given the message as it appears in the ROM, rather than the reformatted version.
[15] Although the message’s text is misquoted by Krakowicz as “YOU’LL NEVER CRACK IT.”
Acknowledgments
The authors would like to acknowledge the support of research associate Owen Brierley (Computational Media Design, The University of Calgary), the editors of Game Studies, and the reviewers who provided detailed comments on our article. John Aycock’s work is supported in part by a grant from the Natural Sciences and Engineering Research Council of Canada.
References
Aarseth, Espen. (1997). Cybertext: Perspectives on Ergodic Literature. Baltimore, MD: Johns Hopkins University Press.
Altice, Nathan. (2015). I Am Error: The Nintendo Family Computer / Entertainment System Platform. Cambridge, MA: MIT Press.
Aycock, John. (2015). “Stringlish: Improved English string searching in binary files.” Software: Practice & Experience, 45 (11). 1591-1595.
----, Reinhard, Andrew, & Therrien, Carl. (2019) A Tale of Two CDs: Archaeological Analysis of Full-Motion Video Formats in Two PC Engine/TurboGrafx-16 Games. Open Archaeology, 5(1), pp. 350-364.
---- (2014). “Strung out: Printable strings in Atari 2600 games.” Tech. Rep. No. 2014-1062-13. Calgary, AB: University of Calgary, Department of Computer Science.
Bailey, W. R. (2008). Hacks, mods, Easter eggs, and fossils: Intentionality and digitalism in the video game. In Z. Whalen & L. N. Taylor (Eds.), Playing the past: History and nostalgia in video games (pp. 69-90). Nashville, TN: Vanderbilt University Press.
Bogost, Ian. (2016). Play Anything: The Pleasures of Limits, the Uses of Boredom, and the Secret of Games. New York, NY: Basic Books.
---- (2015). How to Talk about Videogames. Minneapolis, MN: University of Minnesota Press.
---- (2006). Unit Operations: An Approach to Videogame Criticism. Cambridge, MA: MIT Press.
Consalvo, M. (2007). Cheating: Gaining advantage in videogames. Cambridge, MA: MIT Press.
The Cutting Room Floor. (n.d.). Donkey Kong (arcade). Retrieved April 2, 2018, from https://tcrf.net/Donkey_Kong_(Arcade).
Fernández-Vara, C. (2015). Introduction to game analysis. New York: Routledge.
Feyerbend, Paul. (1962). “Explanation, Reduction and Empiricism.” H. Feigl and G. Maxwell, Eds. Scientific Explanation, Space, and Time. Minneapolis: University of Minnesota Press. 28-97.
Fries, E. (2010, July 31). Halo for the 2600 released at CGE! Download the game here! [Msg 6]. Message posted to http://atariage.com/forums/topic/166916-halo-for-the-2600-released-at-cge-downlo.
Genette, G. (1997). Paratexts: Thresholds of interpretation (J. E. Lewin, Trans.). Cambridge, MA: Cambridge University Press. (Original work published 1987)
Gould, Stephen J. (2002) The Structure of Evolutionary Theory. Cambridge, MA: Harvard University Press.
---- (2000) Crossing Over: Where Art and Science Meet. New York, NY: Three Rivers Press.
Hayles, N. Katherine. (2012) How We Think: Digital Media and Contemporary Technogenesis. Chicago, IL: University of Chicago Press.
---- (2005) My Mother was a Computer: Digital Subjects and Literary Texts. Chicago, IL: University of Chicago Press.
Kolbe, Winrich, Dir. “Darmok.” (1991) Star Trek: The Next Generation. Season 5, Episode 2.
Krakowicz. (n.d.) Krakowicz’s kracking korner: The basics of kracking II. Retrieved April 2, 2018, from http://www.textfiles.com/apple/CRACKING/krckwczt.app..
Kuhn. Thomas. (1962) The Structure of Scientific Revolutions. Chicago, IL: University of Chicago Press.
Lederle-Ensign, Dylan, Robinson, William, Pagnutti, Johnathan, & Mateas, Michael. (2015). A Software Studies Approach to Interpreting Passage. Proceedings of the 10th International Conference on the Foundations of Digital Games. http://www.fdg2015.org/papers/fdg2015_paper_46.pdf.
Lunenfeld, P. (1999). The Digital Dialectic: New Essays on New Media. Cambridge, MA: MIT Press.
Maher, Jimmy. (2012) The Future was Here: The Commodore Amiga. Cambridge, MA: MIT Press.
McGann, Jerome. (2001) Radiant Textuality: Literature Since the World Wide Web. London: Palgrave / St. Martin’s.
McKerrow, R.B. (1939) Prolegomena for the Oxford Shakespeare: A Study in Editorial Method. Oxford: Oxford University Press.
---- (1927) An Introduction to Bibliography for Literary Students. Oxford: Oxford University Press.
MITRE. (2014). CWE-226: Sensitive information uncleared before release. Retrieved April 2, 2018, from https://cwe.mitre.org/data/definitions/226.html.
Montfort, N., & Bogost, I. (2009). Racing the Beam: The Atari Video Computer System. Cambridge, MA: MIT Press.
Murray, Janet. (1997). Hamlet on the Holodeck. Cambridge, MA: MIT Press.
Poster, Mark. (2010) “McLuhan and the Cultural Theory of Media.” Media Tropes Vol 2, No. 2. http://www.mediatropes.com/index.php/Mediatropes/article/view/11931.
---- & Savat, David, Eds. (2009) Deleuze and New Technology. Edinburgh, Scotland. University of Edinburgh Press.
Schoernberger, Erica. (2001) “Interdisciplinary and Social Power.” Progress in Human Geography. Vol 25, Iss. 3, 365-382.
Snow, Charles Percy. (1959). The Two Cultures. Cambridge, UK: Cambridge University Press.
Therrien, Carl. (2019) The Media Snatcher: PC / Core / Turbo / Engine / Grafx / 16 / CDROM2 / Super / Duo / Arcade / RX. Cambridge, MA: MIT Press.
Turkle, Sherry. (2015). Reclaiming Conversation: The Power of Talk in a Digital Age. New York, NY: Penguin Press.
---- (1984) The Second Self: Computers and the Human Spirit. Cambridge, MA: MIT Press.
---- (2011) Alone Together. New York, NY: Basic Books.
---- (2009) Simulation and Its Discontents. Cambridge, MA: MIT Press.
---- (1995) Life on the Screen: Identity in the Age of the Internet. New York, NY: Simon and Schuster.
Willumsen, Ea Christina. (2017) Source Code and Formal Analysis: A Reading of Passage. Transactions of the Digital Games Research Association, 3(2), pp. 213-235.
Ludography
Atari. (1982). Combat Two. [Atari 2600], unpublished prototype.
Darmok2. https://sourceforge.net/projects/darmok2/.
Jensen, P. A. (1990). Geo-Race U.S.A. [Apple II], USA: Mastery Development.
Lubeck, O. (1982). Cannonball Blitz. [Apple II], USA: Sierra On-Line.
Mirsky, R. (1985). Mr. Do! [Apple II], USA: Datasoft.
Neubauer, D. (1986). Solaris. [Atari 2600], USA: Atari.
Nintendo. (1981). Donkey Kong. [Arcade], Japan: Nintendo.
Schwartz, M. (1983). Chase the Chuck Wagon. [Atari 2600], USA: Spectravision.